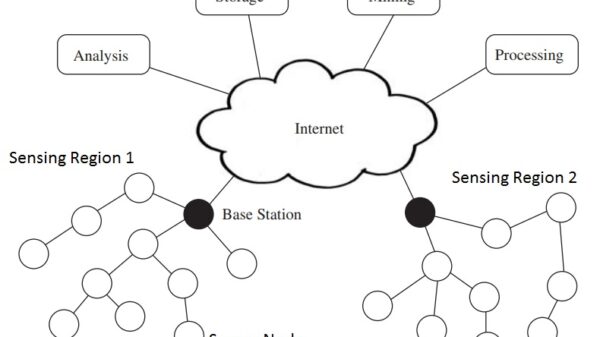
The role of cyber intelligence in today’s cybersecurity landscape is becoming increasingly important. As the sophistication and frequency of cyberattacks continue to grow, organizations need to be able to collect, analyze, and act on threat intelligence in order to protect themselves.
Cyber intelligence is information about potential or current threats to an organization’s information systems and data. It can come from a variety of sources, including:
- Open-source intelligence (OSINT): This type of intelligence is gathered from publicly available sources, such as news articles, social media posts, and technical forums.
- Human intelligence (HUMINT): This type of intelligence is gathered from human sources, such as informants or undercover agents.
- Technical intelligence (TECHINT): This type of intelligence is gathered from technical sources, such as network traffic data and malware samples.
Cyber intelligence can be used to:
- Identify potential threats: By analyzing threat intelligence, organizations can identify potential threats to their information systems and data. This information can then be used to develop mitigation strategies.
- Track the activities of threat actors: By tracking the activities of threat actors, organizations can gain a better understanding of their motivations and capabilities. This information can then be used to develop more effective defenses.
- Respond to incidents: In the event of a cyberattack, cyber intelligence can be used to help organizations respond to the incident more effectively. This information can be used to identify the attacker, track their movements, and disrupt their activities.
Cyber intelligence is a valuable tool that can help organizations protect themselves from cyberattacks. However, it is important to note that cyber intelligence is not a silver bullet. It is just one part of a comprehensive cybersecurity strategy.
Here are some of the benefits of using cyber intelligence:
- Increased visibility: Cyber intelligence can help organizations gain increased visibility into the threat landscape. This can help them identify potential threats and vulnerabilities, and take steps to mitigate them.
- Improved decision-making: Cyber intelligence can help organizations make better decisions about their cybersecurity posture. This can help them allocate resources more effectively and prioritize security risks.
- Enhanced collaboration: Cyber intelligence can help organizations collaborate more effectively with other organizations, such as law enforcement and government agencies. This can help them share information and resources, and coordinate their response to cyberattacks.
Despite the benefits of cyber intelligence, there are also some challenges associated with its use. These challenges include:
- Data quality: The quality of cyber intelligence data can vary significantly. This can make it difficult to identify and assess threats.
- Data volume: The volume of cyber intelligence data can be overwhelming. This can make it difficult to collect, store, and analyze the data.
- Data sharing: There are legal and regulatory challenges associated with sharing cyber intelligence data. This can make it difficult to share information with other organizations.
Despite the challenges, the benefits of using cyber intelligence far outweigh the risks. Organizations that can effectively collect, analyze, and act on cyber intelligence will be in a much better position to protect themselves from cyberattacks.
Here are some best practices for using cyber intelligence:
- Start with a clear understanding of your organization’s needs: What types of threats are you most concerned about? What information do you need to make informed decisions about your cybersecurity posture?
- Build a strong relationships with other organizations: This includes law enforcement, government agencies, and other businesses. These relationships can help you share information and resources, and coordinate your response to cyberattacks.
- Invest in the right tools and technologies: There are a number of tools and technologies that can help you collect, analyze, and store cyber intelligence data. These tools can help you make better decisions about your cybersecurity posture.
- Continuously monitor the threat landscape: The threat landscape is constantly changing. You need to continuously monitor the threat landscape to identify new threats and vulnerabilities.
- Train your employees: Your employees are your first line of defense against cyberattacks. You need to train them to identify and report suspicious activity.
By following these best practices, you can improve your organization’s ability to collect, analyze, and act on cyber intelligence. This will help you protect your organization from cyberattacks.